Decentralized Identifiers (DIDs)
With SSI, individual identity holders create and fully control their identities without the need to seek authorization from an intermediary or centralized authority. This gives them control over how their personal data is shared and used. People have a way to generate and control unique identifiers.
General vision of the system
Source: W3C DID CORE
DID
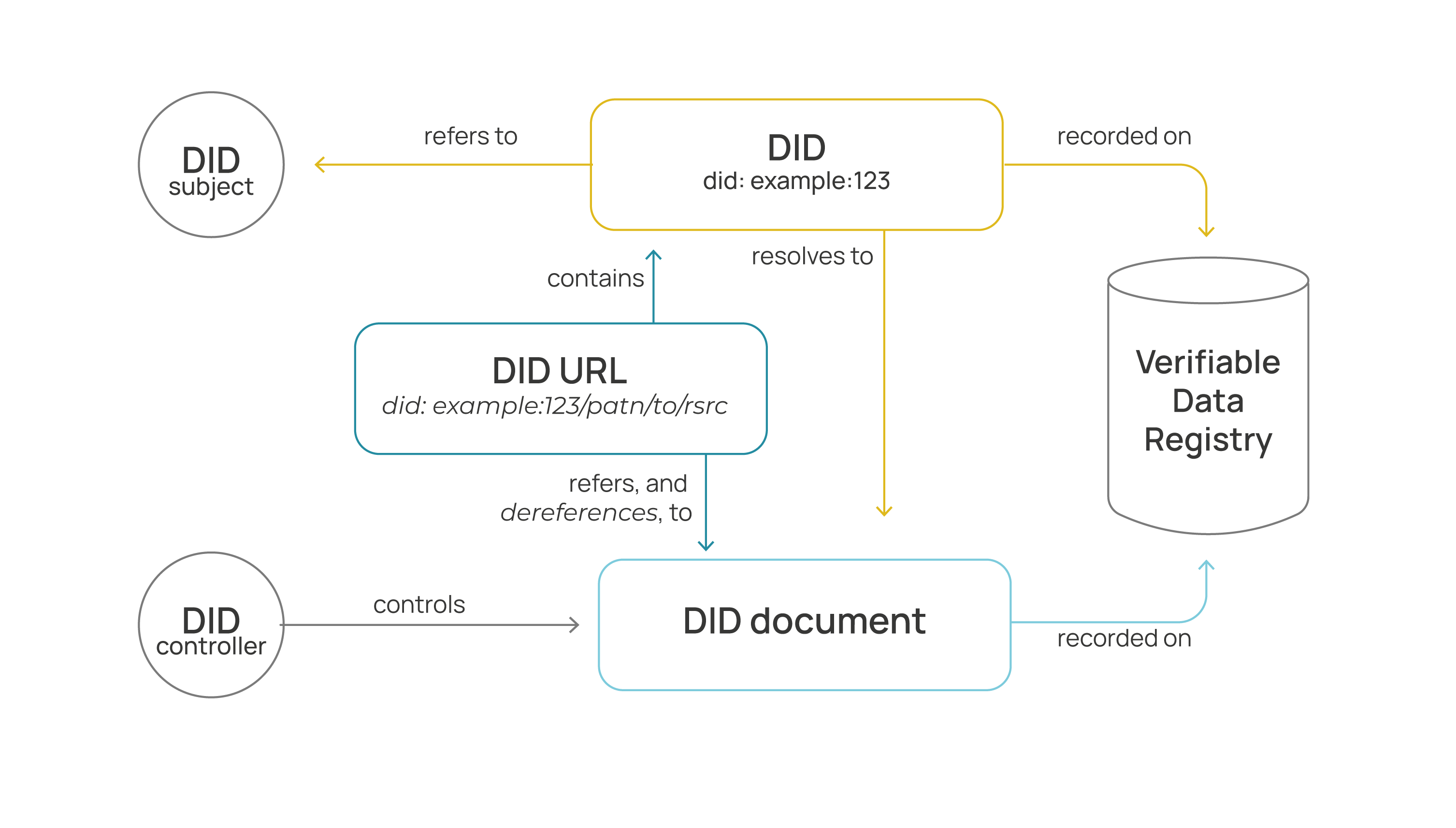
Decentralized Identifiers (DID) are a new type of identifier that enables verifiable and decentralized digital identity. Unlike typical federated identifiers, DIDs are designed to be unlinkable from centralized registries, identity providers, and certification authorities. This allows the controller of a DID to have full control over it without requiring permission from any other party.
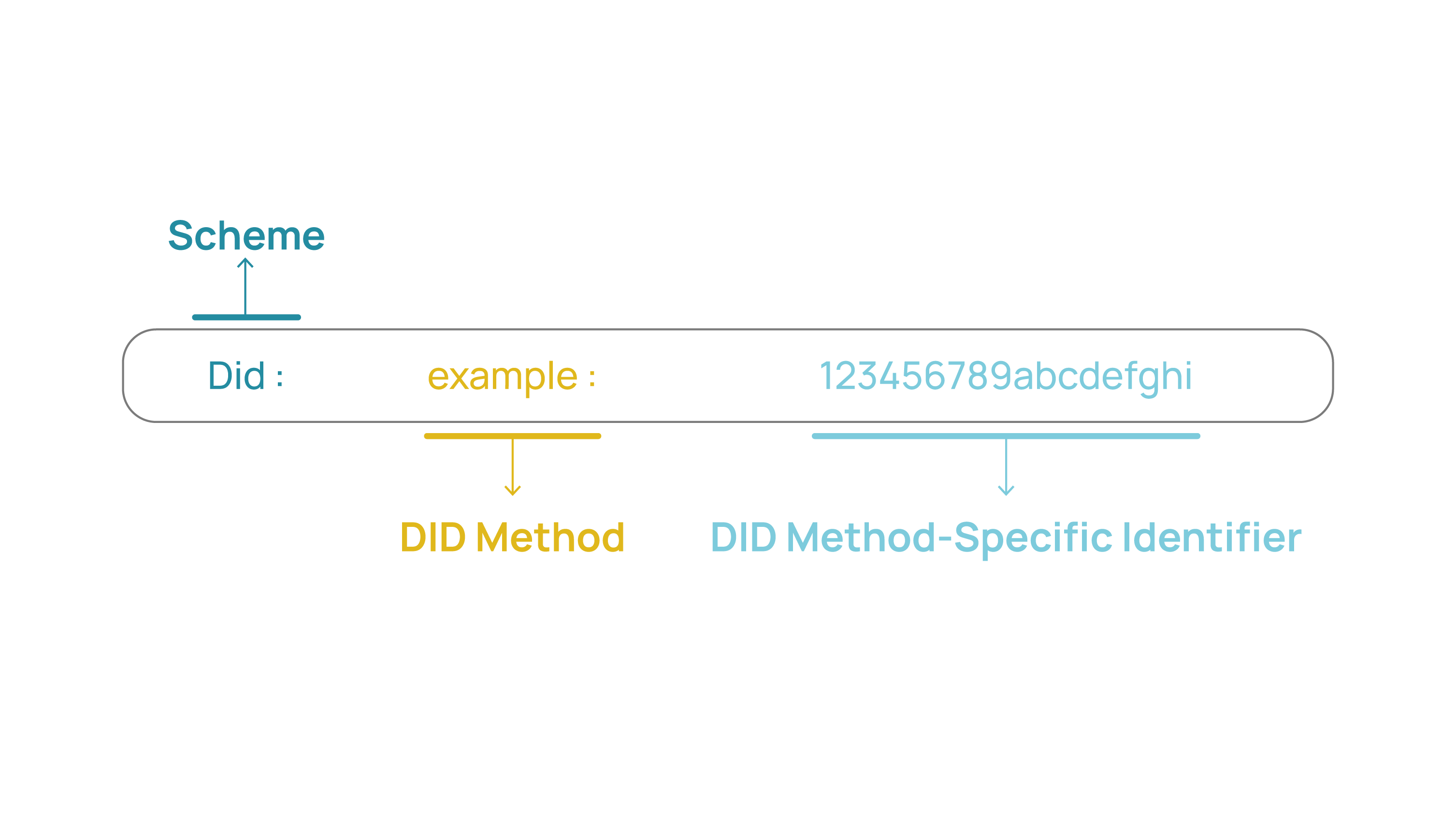
Essentially, DIDs are unique identifiers associated with a subject. A DID is fully defined by three parts:
- Scheme: This part lets us know that what follows is a DID.
- DID Method: It informs us how to interpret the identifier that follows, with its meaning specific to the DID Method used. Two identical identifiers with different DID Methods are identifying different subjects.
- Identifier: The unique character sequence for that specific DID Method, which allows us to uniquely identify the associated DID Document.
DID Method
There are multiple ways to manage DIDs, each of them specified in a particular DID Method. DID Methods are the mechanism through which a specific type of DID and its associated DID Document are created, resolved, updated, and deactivated.
In summary, each DID Method has its own set of rules and protocols for the creation and management of DIDs, which may include how they are registered, how they are resolved (i.e., how the information associated with a DID is found), and how they are updated or revoked.
DID Documents
DIDs can be resolved to an associated DID Document. This document contains all the information associated with a DID. Typically, it expresses verification methods such as cryptographic public keys and relevant services for interactions with the subject of the DID.
DID Subjects
The subject of a DID (DID Subject) is the entity identified by the DID. A DID Subject refers to any entity, whether it be a person, organization, thing, data model, abstract entity, etc. The DID Subject is determined by the DID Controller.
DID Controllers
The controller of a DID (or DID Controller) is the entity (person, organization, or autonomous software) that has the capability, as defined by a DID Method, to make changes to a DID document.
This capability is typically asserted through control of a set of cryptographic keys used by the software acting on behalf of the controller, although it can also be asserted through other mechanisms.
It is important to note that a DID can have more than one controller, and the DID subject can be the DID controller or one of them. For example, an adult could be the controller of their own identity. In this case, the DID Controller is the same as the DID Subject. However, a child could be the subject identified by the DID, but their identity is controlled by a guardian until a certain age. In that case, the DID Subject would be the child, while the DID Controller would be the guardian.
DID Resolvers
A DID Resolver is a component of the system that takes a DID as input and produces a compliant DID Document as output. This process is called DID Resolution. These resolvers are often specific to each DID Method.
Verifiable Data Registry
For DIDs to be resolved into DID Documents, they are typically registered in an underlying system or on some kind of network. Regardless of the specific technology used, any system that supports the registration of DIDs and provides the necessary data to produce DID documents is referred to as Verifiable Data Registries. Blockchain systems are commonly used to register and resolve DIDs.