Interactions between DIDs
The SSI system is based on the free exchange of VCs between DID holders. This functionality is achieved through two new components: a Decentralized Web Node (DWN) and the Wallet and Credential Interaction (WACI) protocol, used in conjunction with the DIDComm encryption scheme.
Decentralized Web Nodes
A DWN is essentially a mailbox that receives and stores messages. When creating a DID, we can set it up as a service, allowing anyone who resolves our DID Document to send messages to our DWN. Requests for credential creation, sending credentials, and requests to verify credentials can be done using the WACI protocol by sending encrypted messages with DIDComm to the DWN.
WACI-DIDComm
The WACI protocol sets the foundations for how a credential is issued and presented. On the other hand, DIDComm is an encryption scheme that uses the public and private keys associated with the DIDs of both parties in the interaction to establish a secure communication channel.
Interaction Model
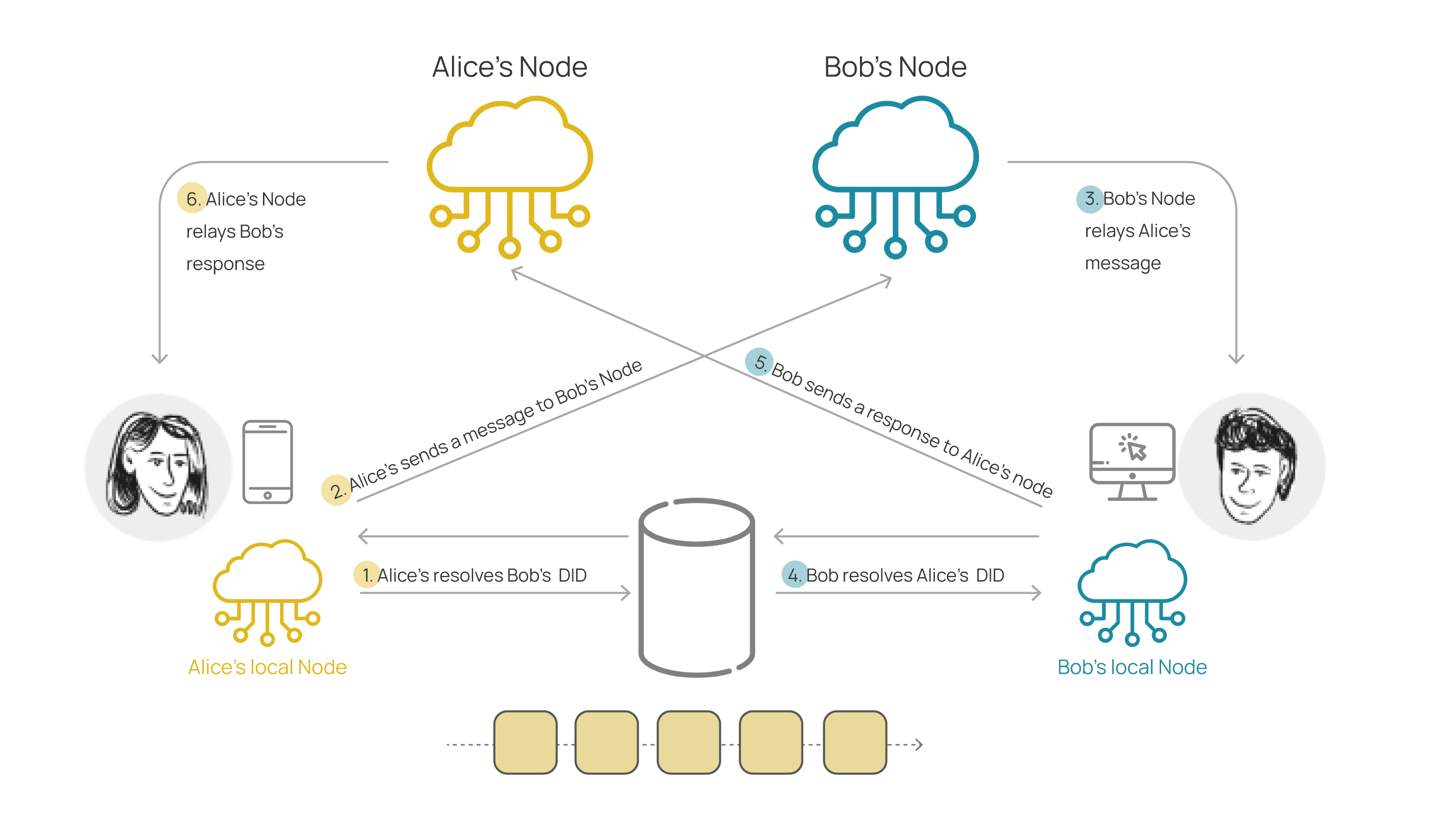
In the following diagram, we will see a typical interaction between two DID holders using DWN:
Source: Decentralised Identity Foundation
Let's use a typical WACI interaction, the presentation of a credential, to illustrate how the system works. Suppose Bob wants Alice to present a citizen credential to entry to an event.
The trigger for the interaction would be that the first party, Alice, discovers Bob's DID. This can be achieved through an Out Of Band message from WACI, where Bob registers his DID and the fact that this message will trigger a presentation exchange. This message can be encoded in a QR code and scanned by Alice at the event entrance.
Next, Alice needs to resolve Bob's DID Document. She can do this by consulting a DID Resolver, such as the Modena component of Extrimian. This will allow Alice to discover Bob's DWN URL and enable her to send messages to him.
The next step would be sending the first message of the exchange, the presentation proposal. In this message, Alice informs Bob of her interest in presenting her credential and also sends her own DID.
On the other hand, Bob now has Alice's DID and can resolve it to obtain her DWN and send her messages. Additionally, messages from both parties can be encrypted with DIDComm to establish a secure connection since both parties know each other's DID.
Next, Alice and Bob can proceed with the rest of the exchange, where Bob asks Alice to present her credential. Then, Alice presents her credential, and Bob evaluates it to verify its validity.