Verifiable credentials
Verifiable credentials (or VCs) are the digital version of the physical documents that individuals, businesses, and organizations use to identify themselves. VCs work in much the same way as documents, but offer some very important advantages.
In the physical world, a credential might consist of:
- Information related to identifying the subject of the credential (for example, a photo, name, or identification number)
- Information related to the issuing authority (for example, a city government, national agency, or certification body)
- Information related to the type of credential this is (for example, a Dutch passport, an American driving license, or a health insurance card)
- Information related to specific attributes or properties being asserted by the issuing authority about the subject (for example, nationality, the classes of vehicle entitled to drive, or date of birth)
- Evidence related to how the credential was derived
- Information related to constraints on the credential (for example, validity period, or terms of use).
A verifiable credential can represent all of the same information that a physical credential represents. The addition of technologies, such as digital signatures, makes verifiable credentials more tamper-evident and more trustworthy than their physical counterparts.
The word "verifiable" in the terms verifiable credential and verifiable presentation refers to the characteristic of a credential or presentation as being able to be verified by a verifier, as defined in this document. Verifiability of a credential does not imply that the truth of claims encoded therein can be evaluated; however, the issuer can include values in the evidence property to help the verifier apply their business logic to determine whether the claims have sufficient veracity for their needs.
Source: W3C Verifiable Credentials Data Model
Verifiable Presentations
Verifiable presentations are data derived from one or more verifiable credentials, issued by one or more issuers, and shared with a specific verifier. A verifiable presentation is a tamper-proof presentation encoded in such a way that the authorship of the data can be trusted after a process of cryptographic verification.
When generating a verifiable presentation, we encounter another significant advantage: the ability to perform selective disclosure and zero-knowledge proofs. Zero-knowledge proofs are a mechanism that allows us to prove that we meet a certain requirement without revealing our data. We can generate a zero-knowledge proof using synthesized data from the original VCs but without containing the actual data itself. On the other hand, selective disclosure enables us to show only the minimum and essential data needed to demonstrate that we fulfill a particular condition.
Types of Agents
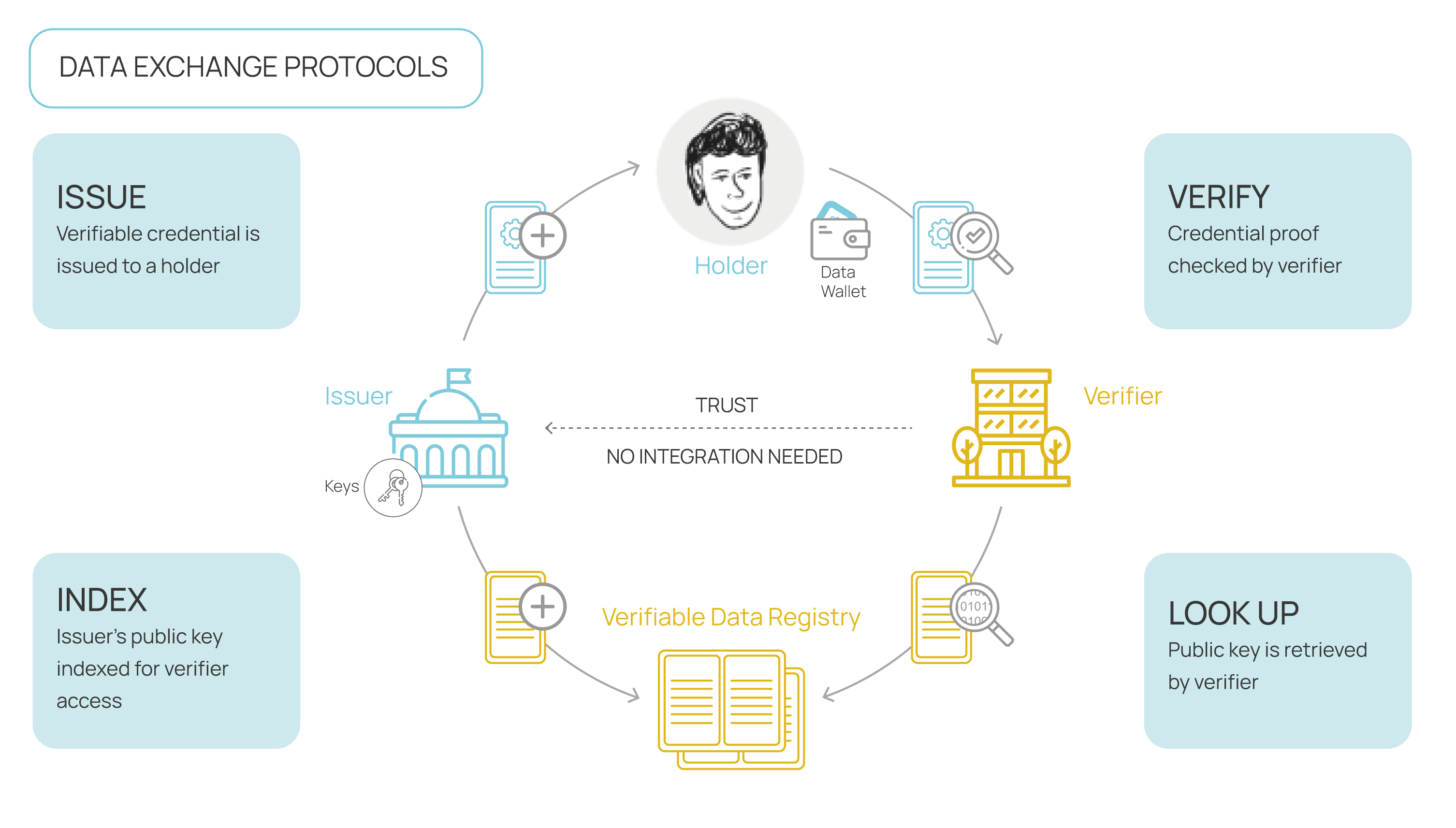
In a credentials exchange, we have three fundamental types of agents:
- Issuer: The entity that issues a VC after receiving proofs from the holder.
- Holder: The individual who carries and manages VCs in their Digital Wallet and presents them to validate their identity.
- Verifier: The entity that verifies the presented credential to validate the identity of the holder.
The interesting aspect of this model is that interactions within the triangle reveal the minimum amount of information while no information is revealed to agents outside the triangle.
Fuente: Trust Over IP
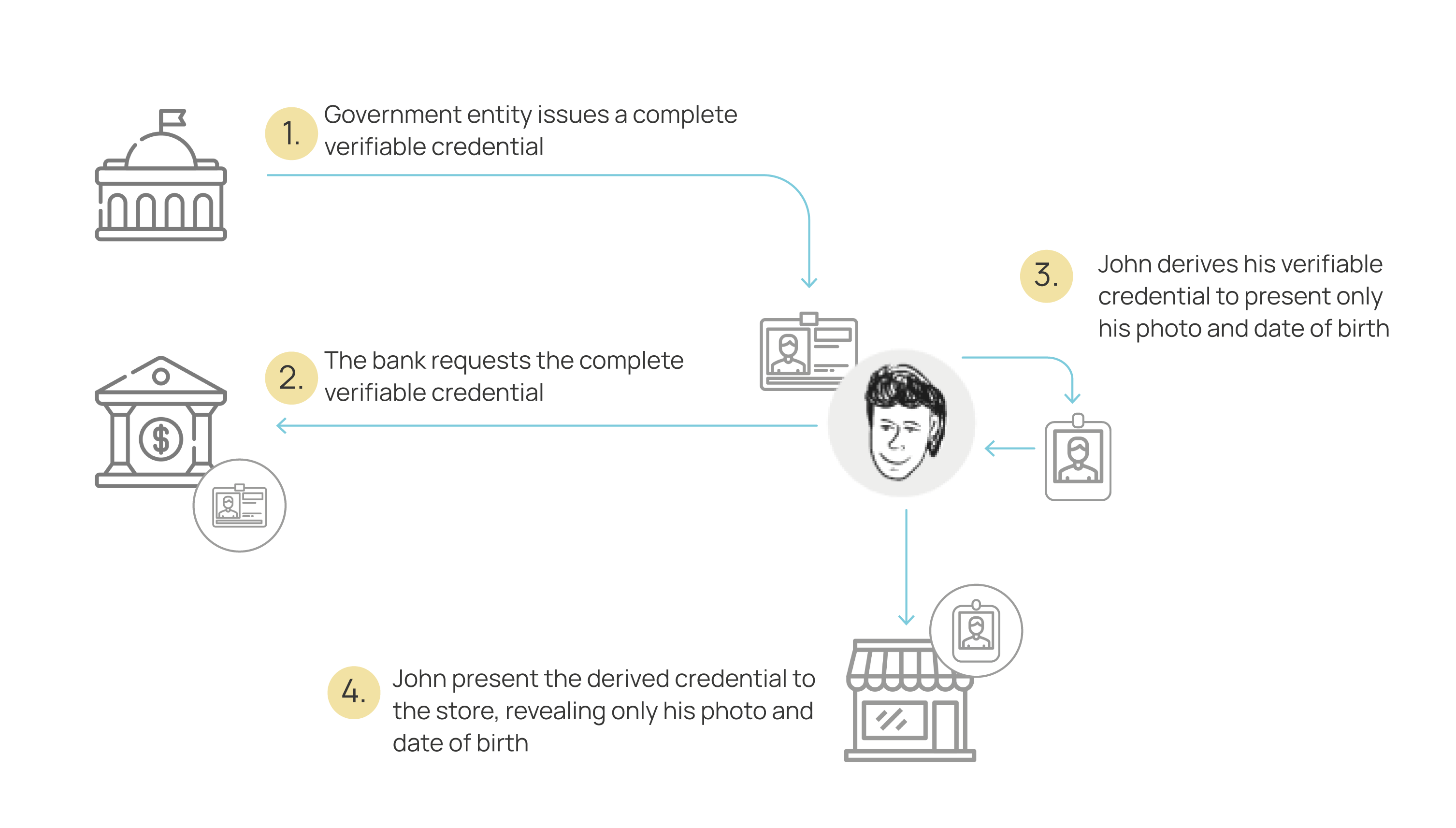
Usage Flow
Below, we can see a complete issuance and presentation flow, where different presentation methods are employed. We can observe how a holder can generate different presentations depending on the occasion, always relying on the same underlying credentials.